Briar
Briar အချက်အလက်စာရွက်
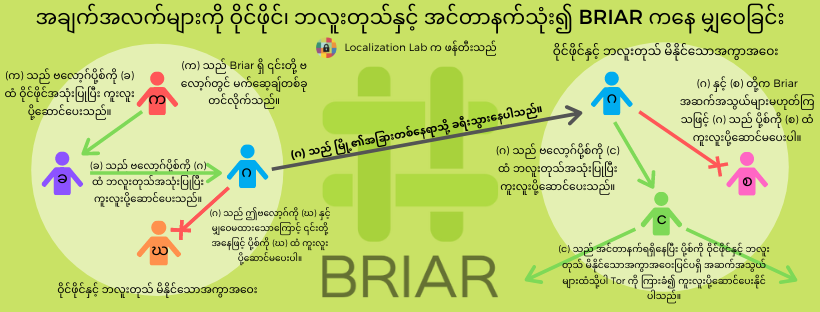
အချက်အလက်များကို ဝိုင်ဖိုင်၊ ဘလူးတုသ်နှင့် အင်တာနက်သုံး၍ Briar ကနေ မျှဝေခြင်း
Surveillance Self-Defense Guides
အခြေခံ | Basics
နည်းပညာလမ်းညွှန်များ | Tool Guides
How to Delete Your Data Securely on Windows (reduced file size version) (text only version)
How to Delete Your Data Securely on Linux (reduced file size version) (text only version)
ထပ်မံသင်ယူစရာများ | Further Learning
လုံခြုံရေးအခြေအနေ | Security Scenarios